What is Two Factor Authentication?
Two-factor Authentication or 2FA is a customer identity confirmation method, where two of the 3 possible factors of verification are incorporated in order to approve accessibility to a website or application.
1) something the user knows; this is often a password, passphrase, PIN, or secret question.
2) something the user has; this entails getting in a one-time password created by a hardware authenticator. Users carry around an authentication device that will certainly create a one-time password on command. Users after that validate by providing this code to the organization.
OR
3) something the user is, this 3rd authentication factor requires the user to authenticate using biometric data. This can include fingerprint scans, face scans, behavioral biometrics, and more.
What are Authentication factors?
There are numerous ways in which a person can be authenticated using greater than one verification method. Authentication factors, detailed in approximate order of adoption for computer, consist of the following:
- Knowledge factor:
Acknowledge factor is something the user recognizes, such as a password, a personal identification number (PIN), or some other type of shared secret.
- Location factor:
A location factor is usually signified by the location from which an authentication attempt is being made.
- Time factor:
A time factor limits user verification to a particular time window in which logging on is allowed as well as restricts accessibility to the system outside of that window.
How do 2FA works?
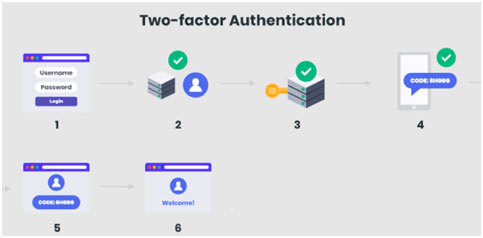
Procedures vary amongst the various 2FA methods, however, a regular 2FA transaction occurs such as this:
The user logs in to the website or service with their username as well as password. The password is confirmed by an authentication server and also, if proper, the user comes to be qualified for the second factor.
The authentication server sends out a unique code to the user’s second-factor approach (such as a smartphone application). The user validates their identification by supplying the added authentication for their second-factor method.
Common Types Of 2FA
Several sorts of two-factor verification are in usage today; some might be stronger or more complex than others, yet all provide far better defense than passwords alone. Here are discussed some common types of Two Factor Authentication.
- Hardware Tokens for 2FA
Probably the oldest kind of 2FA, hardware tokens are little, like a key fob, and generate a new numeric code every 30-seconds. When a user attempts to access an account, they glance at the device and also enter the shown 2FA code back into the website or app.
- SMS Text-Message and Voice-based 2FA
SMS for two-factor verification sends out a login code to a mobile phone number you register with the account. This is the most structured form of 2FA. All you need is a cellphone and also a link to a wireless network. Similarly, voice-based 2FA immediately dials an individual and also verbally supplies the 2FA code.
- Software Tokens for 2FA
One of the most prominent types of two-factor authentication and also a recommended choice for SMS and voice use is a software-generated time-based, one-time passcode.
First, a user has to download and install and set up a totally free 2FA application on their smartphone or computer. At sign-in, the individual first get in a username and password, and then, when prompted, they enter the code shown on the app.
- Push Notifications for 2FA
Rather than depending on the receipt and access of a 2FA token, websites, as well as applications, can now send out the user a push alert that an authentication attempt is taking place.
The device owner just checks out the information and can approve or refute gain access with a single touch. It’s password-less verification without codes to enter, as well as no added communication is required.
Push notification removes any type of opportunity for phishing, man-in-the-middle strikes, or unapproved accessibility. But it just collaborates with an internet-connected device, one that has the ability to install apps.